Exploring how advanced technologies are reshaping the logistics industry and enhancing supply chain efficiency.
Introduction
The logistics industry is undergoing a transformative shift driven by rapid technological advancements. With increasing global trade complexities, heightened customer expectations for faster and more transparent services, and the imperative for real-time data, businesses must adopt cutting-edge technologies to remain competitive. This comprehensive guide delves into the emerging technologies revolutionizing logistics, offering in-depth technical insights, practical applications, challenges, and strategic considerations for implementation.

The future of logistics is connected and powered by AI.
1. Advanced Shipment Tracking Systems
Real-Time Visibility and Transparency
Modern shipment tracking leverages Global Positioning Systems (GPS), Geofencing, and Real-Time Location Systems (RTLS) to provide precise tracking information.
Technical Implementation:
- GPS Integration: Embedding GPS modules in vehicles for continuous location updates.
- Geofencing: Establishing virtual perimeters using coordinate data to trigger alerts upon entry or exit.
- RTLS: Utilizing technologies like Wi-Fi, RFID, or Ultra-Wideband (UWB) for indoor asset tracking.
API Protocols Used in Integration:
- RESTful APIs: Facilitate communication between tracking devices and backend servers.
- MQTT (Message Queuing Telemetry Transport): Lightweight messaging protocol ideal for IoT devices with limited bandwidth.
- Webhooks: Enable real-time data push notifications to client applications.
Benefits:
- Enhanced Customer Experience: Accurate delivery times improve trust and satisfaction.
- Operational Efficiency: Real-time data allows dynamic route adjustments based on traffic or weather conditions.
Challenges:
- Data Volume Management: Handling and storing large amounts of tracking data.
- Integration with Legacy Systems: Ensuring compatibility with existing infrastructure.
2. Internet of Things (IoT) and RFID Technology
Connecting the Supply Chain
IoT devices and Radio-Frequency Identification (RFID) tags are integral for monitoring goods throughout the supply chain.
Technical Implementation:
- Sensor Types and Protocols:
- Environmental Sensors: Temperature (PT100, thermocouples), humidity (capacitive sensors), shock (accelerometers).
- Communication Protocols:
- Short-Range: Bluetooth Low Energy (BLE), Zigbee.
- Long-Range: LoRaWAN, Narrowband IoT (NB-IoT).
- Cellular: LTE-M, 5G networks for wide coverage.
- Edge Processing:
- Local data aggregation and preliminary analysis.
- Protocol translation to ensure compatibility with backend systems.
- Real-time analytics for immediate decision-making.
Challenges:
- Interoperability: Ensuring seamless communication between diverse devices.
- Data Management: Handling vast data volumes generated by IoT sensors.
- Security: Protecting data transmitted over various networks.
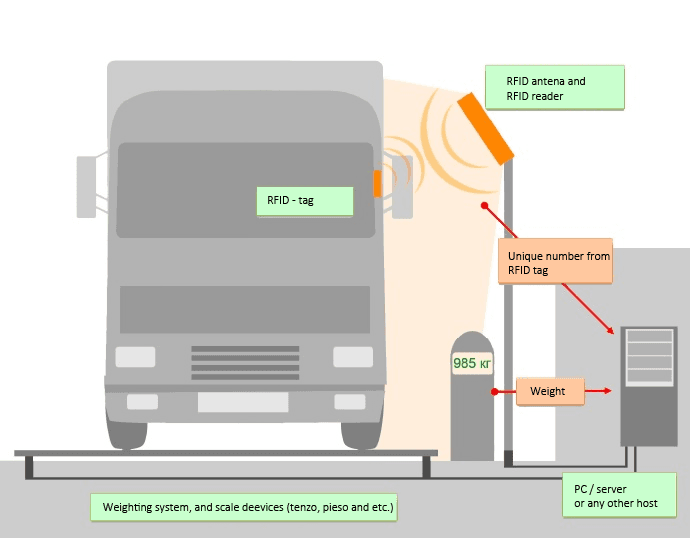
RFID tracking systems used on trucks to track various parts of the supply chains.
3. Artificial Intelligence and Machine Learning
Predictive Analytics and Optimization
AI and ML algorithms analyze large datasets to optimize logistics operations.
Technical Implementation:
- Demand Forecasting Models:
- Time Series Analysis: Using ARIMA models for trends and seasonality.
- Machine Learning Algorithms: Random Forests, Gradient Boosting Machines (GBM) for complex patterns.
- Route Optimization Algorithms:
- Dijkstra's Algorithm: For shortest path calculation.
- Genetic Algorithms: For solving complex, multi-variable optimization problems.
- Ant Colony Optimization: Mimicking ant foraging behavior for path optimization.
Case Study:
- Retailer Implementation: ML-driven forecasting reduced inventory costs by 18% and improved stock availability by 12%.
Challenges:
- Data Quality: High-quality, clean data is crucial for accurate predictions.
- Expertise Required: Need for data scientists and ML engineers.
- Algorithm Bias: Ensuring models do not perpetuate existing biases in data.
4. Automation and Robotics in Warehousing
Streamlining Operations
Automation technologies like Automated Guided Vehicles (AGVs) and Robotic Process Automation (RPA) are revolutionizing warehouses.
Technical Implementation:
- AGVs:
- Navigation Systems: Laser-guided, magnetic tape, vision-based navigation using LIDAR.
- Safety Measures: Collision avoidance sensors, emergency stop mechanisms.
- Automated Sorting Systems:
- Barcode Scanners and OCR: For package identification.
- Conveyor Systems: Integrated with Warehouse Management Systems (WMS).
- Robotic Arms: For picking and placing items with precision.
Integration Challenges:
- System Compatibility: Integrating with existing WMS and ERP systems.
- Scalability: Designing systems that can grow with business needs.
- Workforce Adaptation: Training staff to work alongside automation.

Automated warehouse.
5. Mobile Applications and Platforms
Enhancing Communication and Accessibility
Mobile technology ensures seamless communication among stakeholders.
Technical Implementation:
- Client-Side Implementation:
- State Management: Utilizing Redux or MobX for predictable state changes.
- Offline Capabilities: Implementing local databases like SQLite or Realm.
- Push Notifications: Using Firebase Cloud Messaging or Apple Push Notification Service.
- API Integration:
- GraphQL: For efficient data querying and manipulation.
- WebSockets: For real-time data exchange.
- Authentication: Implementing JWT tokens and OAuth 2.0 for secure sessions.
- Performance Optimization:
- Caching Strategies: To reduce data usage and improve speed.
- Background Processing: Handling tasks without impacting user experience.
- Battery Optimization: Minimizing power consumption through efficient coding practices.
Challenges:
- Device Fragmentation: Ensuring compatibility across various devices and operating systems.
- Security: Protecting sensitive data through encryption and secure coding practices.
- User Experience: Designing intuitive interfaces that enhance productivity.
6. Blockchain Technology
Securing and Simplifying Transactions
Blockchain offers a decentralized ledger enhancing security and transparency.
Technical Implementation:
- Network Architectures:
- Private Blockchains: Restricted networks for internal use.
- Consortium Blockchains: Shared among a group of organizations.
- Public Blockchains: Open networks like Ethereum.
- Consensus Mechanisms:
- Practical Byzantine Fault Tolerance (PBFT): Suitable for permissioned networks.
- Proof of Authority (PoA): Efficient for private networks.
- Proof of Stake (PoS): Energy-efficient alternative to Proof of Work.
- Smart Contracts:
- Frameworks: Solidity for Ethereum, Chaincode for Hyperledger Fabric.
- Testing Tools: Truffle Suite, Hyperledger Composer.
- Security Audits: Using tools like MythX or Oyente to detect vulnerabilities.
Industry Use Cases:
- Walmart's Food Traceability: Enhanced tracking of produce from farm to shelf using IBM's Food Trust blockchain.
- DHL's Verification System: Blockchain-based serialization to prevent counterfeit drugs.
- Port of Rotterdam: Utilizing blockchain for secure digital documentation and efficient customs processing.
Challenges:
- Scalability: Limited transaction throughput compared to traditional databases.
- Integration: Complexity in integrating blockchain solutions with legacy systems.
- Regulatory Compliance: Navigating varying legal requirements across jurisdictions.
7. Data Governance in Logistics
Ensuring Data Quality and Compliance
Effective data governance is essential for managing information assets responsibly.
Framework Components:
- Data Classification:
- Sensitive Data: Personal Identifiable Information (PII), financial records.
- Operational Data: Inventory levels, shipment details.
- Data Lifecycle Management:
- Collection: Establishing protocols for data acquisition.
- Retention Policies: Defining data storage durations based on legal requirements.
- Archival and Deletion: Secure methods for data disposal.
- Compliance Requirements:
- GDPR: For operations involving EU citizens.
- CCPA: California consumer data protection.
- Industry Regulations: E.g., DSCSA for pharmaceuticals.
Implementation Strategies:
- Data Stewardship: Assigning roles for data oversight and accountability.
- Policies and Procedures: Documenting data handling practices and access controls.
- Audit Trails: Maintaining logs for data access and changes for accountability.
Challenges:
- Cultural Change: Encouraging data ownership and responsibility among staff.
- Resource Allocation: Investing in tools and personnel for governance activities.
8. System Architecture and Scalability
Building Robust Infrastructure
A scalable and resilient system architecture is crucial for handling growth and ensuring reliability.
Database Optimization and Scaling:
- Sharding Strategies:
- Horizontal Sharding: Distributing data across multiple databases.
- Range-Based Sharding: Partitioning data based on value ranges.
- Hash-Based Sharding: Using consistent hashing algorithms.
- Directory-Based Sharding: Utilizing lookup tables for shard locations.
- Horizontal Sharding: Distributing data across multiple databases.
- Partitioning Methods:
- List Partitioning: Based on predefined lists of values.
- Range Partitioning: Suitable for time-series data.
- Composite Partitioning: Combining multiple partitioning strategies.
- Replication:
- Master-Slave Configuration: For read scalability.
- Multi-Master Setup: For high availability and write scalability.
- Conflict Resolution: Strategies for eventual consistency models.
Load Balancing:
- Application Layer: Using NGINX or HAProxy.
- Container Orchestration: Kubernetes for managing containerized services.
- Geographic Distribution: Implementing CDNs and global server load balancing.
Monitoring and Observability Tools:
- Metrics Collection: Prometheus for time-series data.
- Logging: ELK Stack (Elasticsearch, Logstash, Kibana) for centralized logging.
- Tracing: Jaeger or Zipkin for distributed tracing.
- Alerting: Integration with PagerDuty or Opsgenie for incident response.
9. Network Infrastructure
Designing Efficient and Secure Networks
Optimizing network architecture enhances performance, security, and reliability.
Edge Computing:
- Local Processing: Reduces latency and bandwidth usage by processing data at the source.
- Edge Nodes: Deployment strategies for IoT devices and gateways.
- Latency Optimization: Critical for applications requiring immediate responses.
Security Zones:
- Demilitarized Zone (DMZ): Separates external-facing services from internal networks.
- Network Segmentation: Dividing networks into segments to contain breaches.
- VPN Architecture: Secure remote access for employees and partners.
Failover and Redundancy:
- Active-Active vs. Active-Passive Setups: Ensuring high availability.
- Geographic Redundancy: Data replication across multiple data centers.
- Disaster Recovery Procedures:
- Recovery Point Objective (RPO): Maximum tolerable period of data loss.
- Recovery Time Objective (RTO): Target time to restore operations.
10. Cache Management Strategies
Optimizing Performance
Effective caching reduces load on databases and improves application performance.
Cache Layers:
- Application Cache:
- In-Memory Caching: Using Redis or Memcached.
- Cache-Aside Pattern: Application logic decides when to cache data.
- Write-Through vs. Write-Behind: Strategies for synchronizing cache with the database.
- CDN Caching:
- Edge Caching: Storing content closer to the user.
- Cache Invalidation Methods: Ensuring users receive updated content.
- Content Versioning: Using unique identifiers for assets to manage cache.
Invalidation Strategies:
- Time-Based Expiration: Setting TTL (Time-To-Live) values.
- Event-Driven Invalidation: Clearing cache upon data changes.
- Cache Stampede Prevention: Implementing locks or request coalescing.
Challenges:
- Cache Consistency: Ensuring data remains accurate across cache and source.
- Cache Overhead: Managing memory usage and potential performance impacts.
11. Continuous Integration and Deployment (CI/CD)
Streamlining Development and Deployment
CI/CD pipelines automate the software release process, enhancing reliability and speed.
Pipeline Components:
- Version Control:
- Branching Strategies: GitFlow, trunk-based development.
- Code Reviews: Implementing pull request workflows.
- Branch Protection: Enforcing policies to maintain code integrity.
- Build Process:
- Automated Builds: Using tools like Jenkins, Travis CI, or CircleCI.
- Dependency Management: Managing libraries and packages.
- Artifact Versioning: Tracking builds with unique identifiers.
- Testing Phases:
- Unit Testing: Validating individual components.
- Integration Testing: Ensuring components work together.
- End-to-End Testing: Testing the application flow from start to finish.
- Load Testing: Assessing performance under stress.
- Deployment:
- Blue-Green Deployment: Running two identical production environments.
- Canary Releases: Gradually rolling out changes to a subset of users.
- Rollback Procedures: Reverting to previous stable versions.
- Feature Flags: Enabling or disabling features without deploying new code.
Challenges:
- Complexity Management: Orchestrating multiple environments and stages.
- Security: Protecting credentials and sensitive data in pipelines.
- Infrastructure as Code: Managing infrastructure configurations programmatically.
12. System Reliability and Fault Tolerance
Ensuring Continuous Operations
Building robust systems requires effective error handling and fault tolerance mechanisms.
Error Management:
- Application Level:
- Circuit Breakers: Preventing failures from cascading.
- Retry Policies: Handling transient errors gracefully.
- Fallback Mechanisms: Providing alternative functionality during failures.
- Infrastructure Level:
- Health Checks: Regularly monitoring service health.
- Auto-Scaling: Dynamically adjusting resources based on demand.
- Service Mesh Implementation: Using Istio for traffic management and resilience.
Monitoring and Alerting:
- Error Rate Thresholds: Defining acceptable error levels.
- Performance Metrics: Tracking latency, throughput, and resource utilization.
- Capacity Planning: Forecasting future resource needs based on trends.
13. Comprehensive Testing Methodologies
Ensuring Quality and Reliability
A robust testing strategy is essential for delivering high-quality software.
Test Types:
- Functional Testing:
- Unit Tests: Verifying individual components.
- Integration Tests: Ensuring components interact correctly.
- System Tests: Testing the entire system as a whole.
- User Acceptance Testing (UAT): Validating against user requirements.
- Non-Functional Testing:
- Performance Testing: Assessing speed and scalability.
- Security Testing: Identifying vulnerabilities (e.g., OWASP Top 10).
- Reliability Testing: Ensuring system stability under various conditions.
- Compliance Testing: Verifying adherence to regulations.
- Specialized Testing:
- IoT Device Testing: Validating sensor data and communication.
- Mobile App Testing: Ensuring functionality across devices.
- API Contract Testing: Verifying API interactions meet specifications.
- Blockchain Smart Contract Testing: Ensuring correctness and security.
Testing Tools:
- Unit Testing: JUnit, pytest, Mocha.
- Automation Testing: Selenium, Appium.
- Load Testing: JMeter, k6.
- Security Testing: ZAP, Burp Suite.
14. Incident Management and Response
Maintaining Operational Continuity
Effective incident management minimizes downtime and impacts on operations.
Response Procedures:
- Detection:
- Monitoring Tools: Real-time alerts from systems like Prometheus, Datadog.
- Anomaly Detection: Identifying unusual patterns or behaviors.
- Classification:
- Severity Levels: Defining incident impact (e.g., critical, high, medium, low).
- Impact Assessment: Evaluating affected services and users.
- Escalation Matrix: Outlining who to notify at each severity level.
- Resolution:
- Runbooks: Step-by-step guides for common issues.
- Communication Protocols: Keeping stakeholders informed.
- Collaboration Tools: Using platforms like Slack or Microsoft Teams.
- Post-Incident:
- Root Cause Analysis (RCA): Identifying underlying issues.
- Corrective Actions: Implementing fixes to prevent recurrence.
- Documentation Updates: Updating policies and procedures.
Challenges:
- Coordination: Managing cross-team communication during incidents.
- Time Sensitivity: Rapid response is critical to minimize impact.
- Continuous Improvement: Learning from incidents to enhance systems.
15. Cost Analysis and Optimization
Balancing Investment and Efficiency
Understanding and managing costs is crucial for sustainable operations.
Infrastructure Costs:
- Compute Resources: Costs per virtual machine or container instance.
- Storage: Charges per gigabyte for data storage.
- Network Transfer: Expenses associated with data transfer between services.
- Licensing Fees: Costs for proprietary software and tools.
Optimization Strategies:
- Resource Right-Sizing:
- Utilization Monitoring: Adjusting resources based on actual usage.
- Auto-Scaling Policies: Scaling resources dynamically.
- Reserved Instances: Committing to usage for cost savings.
- Cost Allocation:
- Tagging Resources: For tracking and attribution.
- Chargeback Models: Assigning costs to departments or projects.
- ROI Calculations: Evaluating return on investments.
- Optimization Tools:
- Cloud Cost Analyzers: Tools like AWS Cost Explorer, Azure Cost Management.
- Resource Utilization Monitors: Identifying underutilized resources.
- Waste Identification: Detecting idle or orphaned resources.
Challenges:
- Predicting Costs: Variability in cloud usage can complicate forecasting.
- Balancing Performance and Cost: Ensuring cost savings do not degrade service quality.
16. Modern Architecture Patterns
Adopting Contemporary Solutions
Embracing modern architectural practices enhances agility, scalability, and maintainability.
Containerization:
- Docker: Packaging applications and dependencies into portable containers.
- Kubernetes: Orchestrating container deployment, scaling, and management.
- Service Mesh:
- Traffic Control: Managing how requests are routed.
- Security: Implementing mTLS for secure communication.
- Observability: Gaining insights into system behavior.
Microservices Architecture:
- Service Boundaries: Defining clear responsibilities for each service.
- Inter-Service Communication:
- Synchronous: RESTful APIs, gRPC.
- Asynchronous: Messaging systems like RabbitMQ, Apache Kafka.
- API Gateway Patterns:
- Functionality: Request routing, protocol translation, aggregation.
- Tools: Kong, AWS API Gateway, NGINX.
- Event-Driven Architecture:
- Benefits: Loose coupling, scalability, resilience.
- Implementation: Using event buses or streaming platforms.
Challenges:
- Complexity Management: Increased complexity over monolithic architectures.
- Distributed Systems Issues: Handling network latency, partial failures.
- Operational Overhead: Requires sophisticated monitoring and management tools.
17. Decision Framework for Technology Adoption
Making Informed Choices
Implementing new technologies requires strategic planning and analysis.
Framework Steps:
- Assess Needs:
- Identify operational challenges and strategic objectives.
- Engage stakeholders to understand requirements.
- Research Solutions:
- Evaluate technologies and vendors.
- Consider scalability, compatibility, and support.
- Pilot Programs:
- Implement small-scale tests.
- Collect data on performance and integration challenges.
- Cost-Benefit Analysis:
- Calculate Total Cost of Ownership (TCO) and Return on Investment (ROI).
- Assess both quantitative and qualitative benefits.
- Implementation Planning:
- Develop detailed project plans.
- Allocate resources and define timelines.
- Continuous Evaluation:
- Monitor KPIs and adjust strategies as needed.
- Solicit feedback from users and stakeholders.
Considerations:
- Risk Management: Identify potential risks and develop mitigation plans.
- Compliance: Ensure adherence to legal and regulatory requirements.
- Change Management: Prepare the organization for transitions.
18. Conclusion
The logistics industry is at the cusp of a technological revolution. By thoughtfully integrating advanced technologies like IoT, AI, blockchain, and adopting modern architectural practices, businesses can achieve significant improvements in efficiency, security, and customer satisfaction. Success in this endeavor requires not only technical expertise but also strategic planning, effective governance, and a culture of continuous improvement.
At Mirage Metrics, we specialize in delivering advanced data analytics solutions tailored specifically for the logistics industry. Our expertise lies in transforming complex data into actionable insights that drive cost savings and operational efficiency. We partner with organizations to navigate the complexities of technological adoption, ensuring they remain competitive in an increasingly digital world.
Testimonial
"Mirage Metrics didn't just provide us with data—they offered actionable insights that transformed our operations and significantly reduced costs. Their expertise was instrumental in our journey toward efficiency and profitability."
— COO of Transwin
Workforce Management for Logistics Companies is Essential
In the competitive landscape of today, data analytics is no longer a luxury—it's a necessity for logistics companies aiming to reduce costs and stay ahead. By implementing the strategies outlined in this guide, you can unlock significant savings, drive efficiency, and position your company for long-term success.
The question isn't whether you should leverage data analytics—it's how soon you can start reaping the benefits.
Next Steps: Free Consultation Offer
Ready to transform your logistics operations and slash costs by up to 20%?
Mirage Metrics is offering a complimentary consultation to assess your current operations and identify opportunities for cost reduction through advanced data analytics.
👉 Schedule Your Free Data Analytics Consultation Now
Contact Us
- Email: mehdi@miragemetrics.com
- Website: www.miragemetrics.com
- Book Your Call: https://calendly.com/mehdi-mirage/30min
About Mirage Metrics
Mirage Metrics specializes in delivering advanced data analytics solutions tailored for the logistics industry. Our mission is to empower businesses with the insights needed to drive efficiency, reduce costs, and enhance customer satisfaction.
Mirage Metrics—Your Partner in Data-Driven Transformation
19. Technical Glossary
- AES (Advanced Encryption Standard): A symmetric encryption algorithm widely used for secure data transmission.
- ARIMA (AutoRegressive Integrated Moving Average): A statistical analysis model used for time series forecasting.
- CI/CD (Continuous Integration/Continuous Deployment): Practices that enable frequent and reliable code changes.
- Docker: An open-source platform for automating the deployment of applications in containers.
- gRPC: A high-performance, open-source framework for remote procedure calls.
- Istio: An open-source service mesh that provides traffic management, security, and observability.
- JWT (JSON Web Token): A compact token format used for securely transmitting information.
- Kubernetes: An open-source system for automating deployment, scaling, and management of containerized applications.
- MQTT (Message Queuing Telemetry Transport): A lightweight messaging protocol for small sensors and mobile devices.
- mTLS (Mutual Transport Layer Security): An authentication method that ensures both client and server verify each other's identities.
- OAuth 2.0: An authorization framework that enables applications to obtain limited access to user accounts.
- OWASP (Open Web Application Security Project): A nonprofit foundation that works to improve software security.
- PoA (Proof of Authority): A consensus algorithm used in private blockchains.
- PoS (Proof of Stake): A consensus mechanism where validators stake cryptocurrency to participate.
- RESTful API: An API that adheres to the principles of REST (Representational State Transfer).
- RPO (Recovery Point Objective): The maximum tolerable period in which data might be lost.
- RTO (Recovery Time Objective): The target time set for the recovery of IT and business activities after a disaster.
- Zero Trust Security Model: A security concept that requires all users, inside or outside the network, to be authenticated.
Note: This guide is intended for informational purposes. For tailored solutions and professional advice, consult with industry experts.



![Fuel Tracking Systems: The Ultimate Guide to Cutting Logistics Costs [2024 Edition]](https://prod.superblogcdn.com/site_cuid_cm2eekg9r004zm1jllml11hnn/images/image-2-1731338851911-compressed.jpg)